Solutions Technologiques Innovantes
Développement d'applications • Sites Web • IA • Automatisation
Fort de plus de 15 ans d'expérience, nous concevons et déployons des applications sur mesure pour répondre à vos besoins spécifiques.
Nos Services
Nous proposons une gamme complète de services technologiques pour accompagner votre entreprise dans sa transformation numérique.
Développement Web
Sites vitrines, applications web complexes et plateformes e-commerce optimisées pour tous les appareils.
Applications
Applications métier sur mesure, solutions mobiles et logiciels spécialisés pour optimiser vos processus.
Intelligence Artificielle
Agents IA intelligents pour automatiser et optimiser vos processus décisionnels.
Automatisation
Automatisation de tâches répétitives pour accroître votre productivité et réduire les erreurs.
Nos Réalisations
Découvrez quelques-uns de nos projets récents qui illustrent notre expertise et notre savoir-faire.
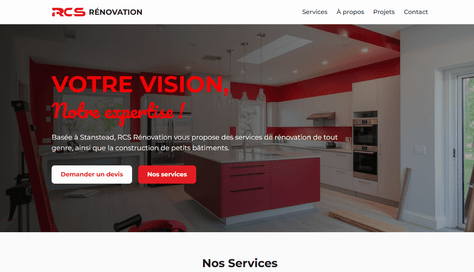
Site Web pour RCS Rénovation
Développement d'un site web vitrine moderne, incluant design et fonctionnalités sur mesure.

Solution IA pour Secteur Financier
Plateforme pour l'automatisation de processus financiers complexes, optimisant la performance des analystes.
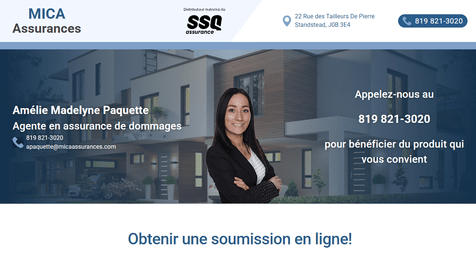
Portail Client MICA Assurances
Plateforme Blazor WASM pour la génération de prospects en assurances auto et habitation.
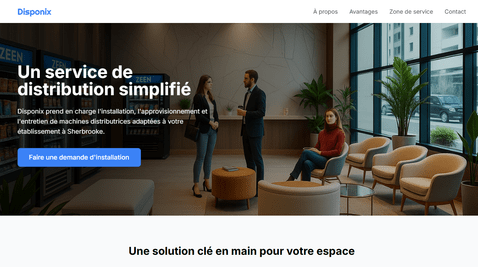
Site Web Vitrine
Conception et développement d'un site web moderne et performant pour un service de distribution automatisée.

Typely - Domain Primitives
Librairie .NET open-source pour la création de types forts avec une API fluente et génération de code.

Portail Client Assurances Stéphane Robichaud
Application Blazor WASM pour la génération de leads en assurances auto et habitation.
Notre Expertise
Plus de 15 ans d'expérience dans le développement de solutions technologiques innovantes.
Écosystème Microsoft
Expertise approfondie en .NET C#, Blazor, Azure et SQL Server pour des applications robustes et évolutives.
Intelligence Artificielle
Création d'agents intelligents et d'automatisations basés sur les modèles de langage (LLM) pour optimiser vos processus métier.
Automatisation & DevOps
Mise en place de pipelines CI/CD et automatisation des processus pour accélérer le développement.
Années d'expérience
Projets réalisés
Technologies maîtrisées
ans en IA appliquée
Approche pragmatique
Notre approche allie rigueur, qualité du code et automatisation afin d'accélérer la productivité et de garantir la fiabilité de nos livrables.
-
Design patterns et architecture évolutive
-
Tests automatisés et intégration continue
-
Solutions sur mesure adaptées à vos besoins
-
Veille technologique et innovation constante
Contactez-nous
Discutons de votre projet et voyons comment nous pouvons vous aider à atteindre vos objectifs.